How We Manage Website and Web Server Security
The WDM vulnerability testing tools available can help ensure that the security of your website is never compromised. This includes not only ensuring that it is protected against cyber attacks but also detecting vulnerabilities in its code or software that might allow hackers to take control of your site leading to the need to hot fixes or upgrades.
When it comes to cyber security, constant web server monitoring also plays a key role in ensuring the safety of your website. WDM can provide you a few reasons as to why you should monitor your server frequently for vulnerabilities software updates, as well as some helpful resources on staff trsining around hacking methods.
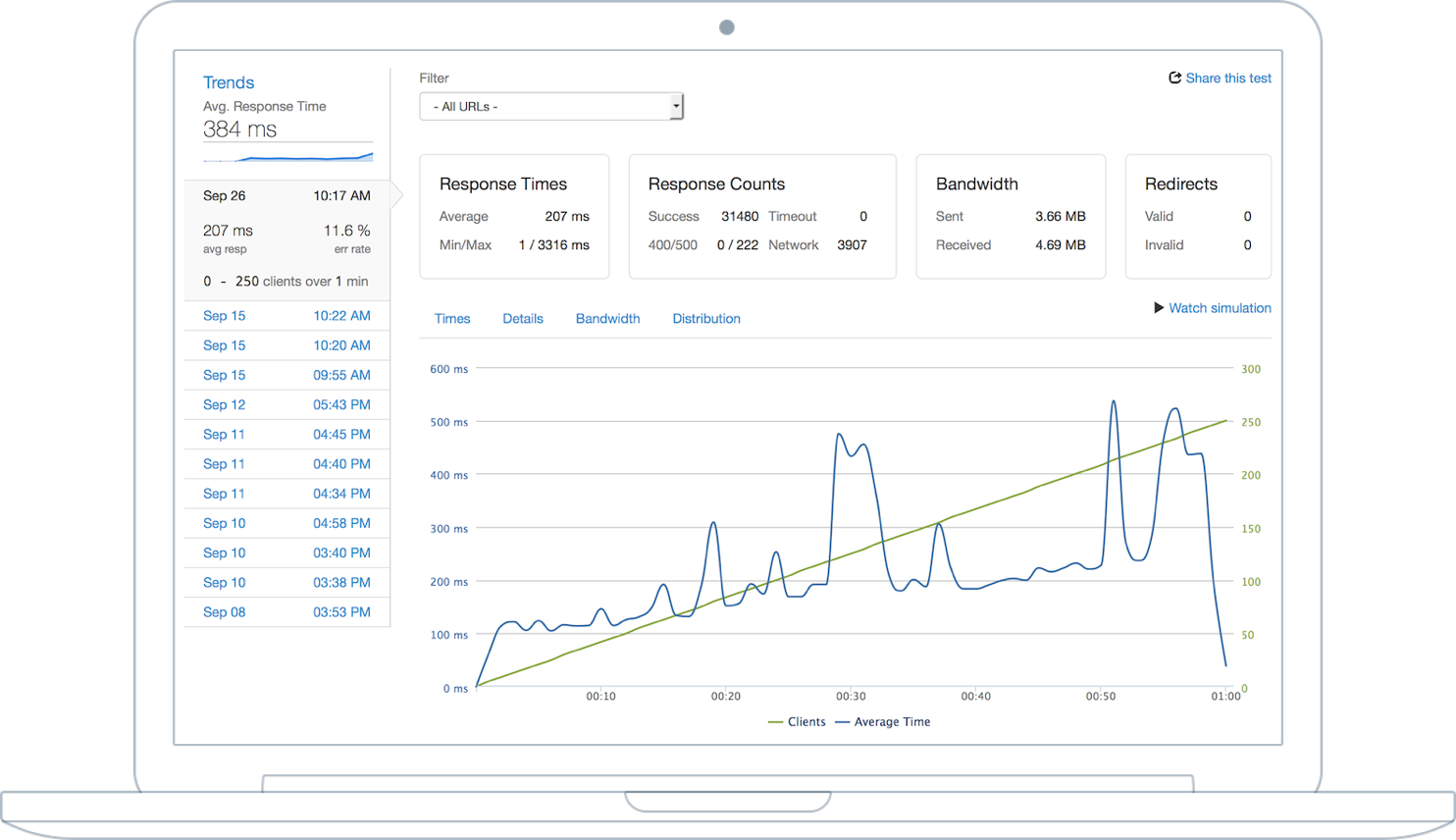
Why You Should Load Test Your Website Before Launching
If you are building a website or application, it is imperative that you do load testing before launching. Load testing allows you to identify any problems in your site's response time and provides useful information on how well your site will work for visitors.
5 Ways How to Keep Your Website & Servers Updated and Patched
1. Use WDM web application penetration testing. It is not about the technology. It is about finding the weakest link in the chain and then stopping hackers exploiting it.
2. WDM and your web application security team needs to be able to work quickly to identify and fix vulnerabilities before attackers exploit them.
3. A website can't be hacked overnight. That is why you need to conduct vulnerability scans on a regular basis.
4. Use the Australian Cyber Security Centre's free training for your staff, WDM vulnerability and penetration testing service for small businesses, Govement, Corporations and web server infrastructure to reduce the risk of a cycber security incident.
5. Contact WDM now or chat withn us online for your cycber security requirements or call us toll free on 1300 308 210.